
Cyber Event Analysis | August 1, 2024
A Closer Look: Unveiling the Global Impact of CrowdStrike Event
CrowdStrike, a leading cybersecurity technology provider, offers a range of products and services, including endpoint detection and response (EDR). EDR monitors traffic passing through computer systems to protect against malicious files, viruses and malware. In its last earnings report, CrowdStrike reported a total of nearly 24,000 organization customers, including nearly 60% of the Fortune 500.
On July 19, at 04:09 am UTC, CrowdStrike released a "Rapid Response Content" update to its EDR tool dubbed “Falcon,” sitting on Microsoft Windows devices. CrowdStrike uses Rapid Response updates to adapt to the changing threat landscape quickly. Unfortunately, this update contained a software coding flaw that caused Microsoft devices to crash, leading to the infamous "blue screen of death." CrowdStrike promptly reverted the update and introduced a fix, but the impact was significant.
The CrowdStrike event highlights the potential severity of digital supply chain interconnectedness, as it disrupted not only CrowdStrike's customers but also propagated through third-party networks, impacting the resilience of seemingly unrelated industries. However, in the immediate aftermath we observe that insurers are carefully considering the implications of this event and continuing to support their clients with unchanged coverage, thus demonstrating the resilience of the cyber insurance market.
Following this incident, Guy Carpenter has estimated the losses and evaluated the implications for underwriting considerations and catastrophe risk management.
A Closer Look: Unveiling the Global Impact of CrowdStrike Event
Measuring the Impact
Ultimately, while the millions of affected devices represent only a small percentage of Microsoft devices, the flawed update caused operational disruptions globally. More than 7,000 flights were canceled or delayed over several days, and disruptions were felt in critical infrastructure sectors such as healthcare, retail, financial services and hospitality. Estimates of the impact are still evolving. At this point, many insureds have filed notices of circumstances, and it is still early in the claims process.
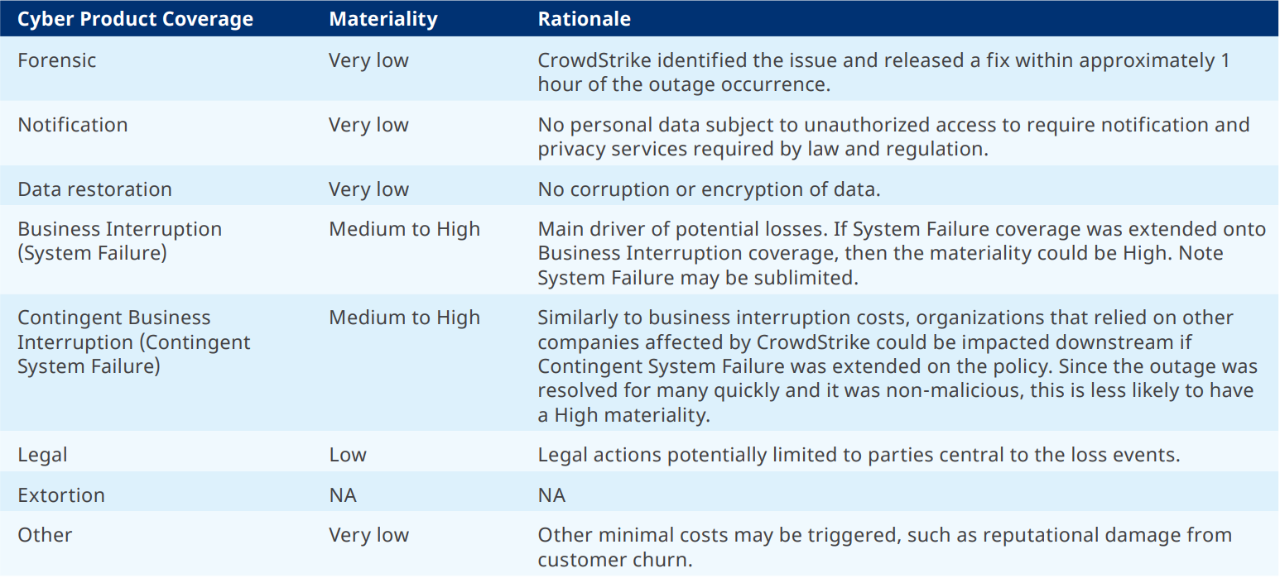
While some cyber catastrophe model vendors contemplate malicious events only, others have accidental event scenarios in their catalogue. These events are not directly comparable to the CrowdStrike outage, but they can form a basis to derive a loss estimate. Notably, the profile of accidental outages known as System Failure lacks many costs that rapidly ramp up in the case of malicious triggers, such as forensic expenses, breach counsel, data restoration and extortion costs.
CrowdStrike’s outage will have insurable loss by triggering some coverage sections, but the non-malicious nature of the disruption limited the breadth of impact a malicious event could have created.
Using this breakdown of impact on coverages, Guy Carpenter developed a 5-step modelling approach, which leverages leading cyber vendor tools, to model the potential loss of the CrowdStrike Falcon outage:
- Analyzing vendors’ catalogues to identify cyber events comparable to the CrowdStrike event.
- Assessing the gap between the identified cyber events in Step 1 and the CrowdStrike incident (e.g., outage duration, malicious versus accidental intent, footprint).
- Adapting the retained event(s) to mimic the CrowdStrike outage by:
- Capturing the technology landscape. In this instance, we contemplated specific versions of Microsoft operating systems and servers in line with the versions that were impacted by the CrowdStrike outage.
- Deriving the corresponding footprint in line with CrowdStrike Falcon market and Microsoft solutions market shares.
- Focusing on events with spreading rates and outage durations close to what we observed post CrowdStrike incident.
- Focusing on Business Interruption and Contingent Business Interruption coverages only to account for the accidental nature of this outage in contrast to its malicious counterpart.
- Computing the losses with different intensities to capture moderate to extreme variations this incident can take.
In addition, pursuant to the vendor guidance for quantifying the CrowdStrike Falcon outage, Guy Carpenter evaluated catalogue scenarios affecting similar technologies and introduced bespoke scalars to adjust the footprint and severity.
We collated the various loss estimates from the different vendors as well as Guy Carpenter’s own estimate. The table below shows the different estimate in absolute and loss ratio terms based on Guy Carpenter’s $15.8 billion gross premium estimate for the cyber insurance industry.
According to Guy Carpenter's estimates, less than 1% of companies globally with cyber insurance were impacted. With a quickly introduced fix, many organizations had the opportunity to mitigate the outage before the waiting period expired for business interruption claims. Typically, those range between 4 to 12 hours in cyber insurance policies. As a result, the likely insured loss is between $300 million and $1 billion. Guy Carpenter's findings align with the conclusion that this event would not result in a material loss for most insurers, although this could change based on the wordings adopted by carriers, concentration of underwriting within affected industry sectors, and uptake of System Failure coverage.
Table 1: CrowdStrike Outage Loss Estimate

Table 2: Assessment of Coverage Scope for CrowdStrike Outage
Underwriting Considerations
Had the event been malicious, the impact would be far greater. Guy Carpenter estimates that a ransomware attack that directly impacts a widely used operating system could have a total impact between $600 million and $2 billion in insurable loss.
If the outage remains limited in scope, it will give greater perspective to underwriting for Business Interruption and System Failure. This technology outage highlights the increased risk faced by organizations that rely on widely deployed software running on a dominant operating system provided by commonly used vendors. Impacted organizations benefitted from a quick response and transparency around the issue. CrowdStrike announced measures to mitigate the risk of future similar disruptions, and this event should serve as a learning moment for all technology providers and their clients.
Underwriters must consider the unique circumstances that led to this outage for developing future risk appetite. First, in this instance, the vendor had high-level privileges to communicate directly with sensors linked to the operating system software. Importantly, most vendors do not have this level of access and, therefore, cannot directly impact the operating environment. This prioritization limits the ability of most software updates to disrupt the environment, which keeps operations more stable and reduces the potential frequency for similarly caused widespread system failures.
Second, automated content updates provide significant value for EDR tools. Regularly providing cybersecurity product updates protects against evolving malicious activity. Delaying such content updates would slow down behavior-based detection and increase the threat of malicious activity, including targeting zero-day vulnerabilities. Accordingly, vendor-initiated system failures are challenging to underwrite.
Ultimately, as long as software and updates remain flawed, insurers will need to consider how technology poses the greatest risk to interconnected failures and how insureds can establish resiliency from such failures. Evaluating how technology dependencies and digital supply chain risk differs by industry and size segments within a portfolio may insulated outsized impacts. The CrowdStrike outage also sheds light on the effectiveness of Waiting Hours retentions within Business Interruption coverages.
Each market loss, especially headline-grabbing events, sharpens the understanding of nuances in quantifying cyber exposure and systemic threats while testing the efficacy of coverage and relevancy of the products. As the market matures, these shots across the bow of sizeable but manageable cat events refine how to best protect capital at each step of the insurance value chain without a doomsday loss quantum.
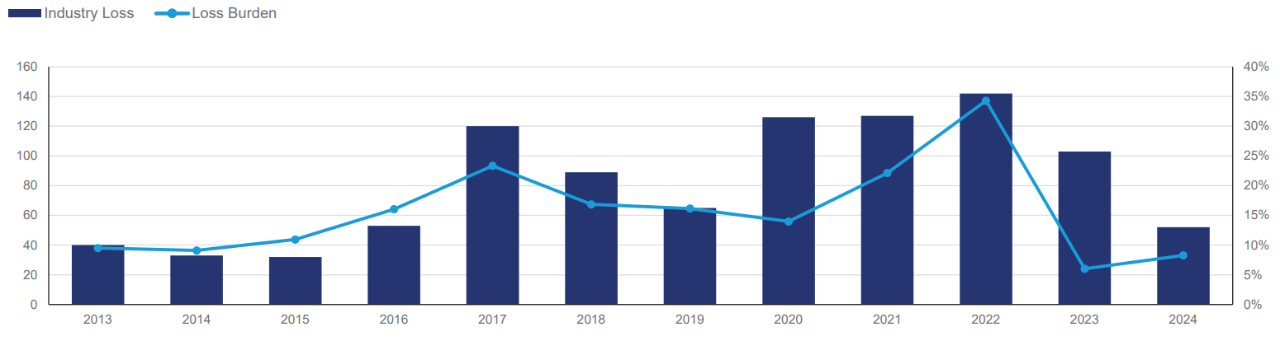
Figure 1: Loss Burden of Largest Individual Property Claim by Year
Shifting View of Cat Risk
As the cyber market continues to mature, the potential for cat events has influenced scenario modeling and reinsurance purchasing trends. However, given the events of the past 18 months, the industry should re-evaluate its perspective of risk and consider the impact of frequency losses alongside the market moving systemic risks. Rather than bracing for the single super cat, perhaps the market should be more concerned with the growing litter of “Kitty Cats”—mid-size events that meet the criteria for a cat loss, but at a smaller scale.
Since May 2023, the cyber market has experienced five Kitty Cats—MoveIT, Change Healthcare, CDK Global, CrowdStrike, and Snowflake—all of which were headline news. While these losses have had limited impact individually, when aggregated into a single treaty period, they could generate a >10% loss ratio impact to the industry, which is more in line with the expectation for a single super cat.
This aligns with cyber catastrophe modeling and scenario analysis, which have focused on events contributing double-digit impacts to loss ratios. As the industry grows and loss coding and reporting continues to improve, market understanding around individual loss burdens from leading events will provide more insight to help manage portfolio aggregation and cat risk. Using the experience from the property world where large individual cat events have contributed 5%-40% to the annual loss burden, the expectation that the cyber market may have to weather several such events in the course of an underwriting year becomes clear.
Kitty Cat events are hard to predict and, therefore, hard to model accurately compared to their super cat counterparts. This is further corroborated as vendor models diverge further in lower return periods than in the tail. Some can be approximated using modified vendor scenarios, but there are no placeholder scenarios available to approximate the loss. As the industry further improves loss coding and reporting for cat events, its understanding of individual loss burdens from leading events will provide clarity on how to best manage losses from these events.
How Guy Carpenter Can Help
The CrowdStrike Falcon incident had a global impact, causing operational disruptions across various sectors. While the exact losses are still being determined, estimates suggest a sizable but manageable insured loss.
Guy Carpenter analytics has provided perspective on the CrowdStrike Falcon incident with a multi-view perspective including:
- Single Point of Failure (SPoF) analysis using tools licensed from KYND and CyberCube that estimate dependencies on CrowdStrike Falcon to see where losses may emerge;
- Modeled View of Loss by leveraging a multi-vendor analysis that quantifies the CrowdStrike financial impact associated with insurer-specific portfolios; and
- Insights from a cybersecurity, claims and underwriting standpoint provided across Marsh.
These capabilities address portfolio nuances, with the ultimate objective of supporting our clients with capital protection solutions. In addition, Guy Carpenter’s proprietary CatStop+ product maintains the flexibility to respond to risk from emerging events, as well as the unfolding uncertainty around cat losses.
Guy Carpenter’s Cyber Center of Excellence is poised to help our clients with tools and expertise to navigate these challenges and optimize their reinsurance strategies.
____________________________________________________________________________________________________________
Cyber Event Analysis | July 19, 2024
A Global Outage with Widespread Impact

On July 19, at 04:09 am UTC, cybersecurity company CrowdStrike released a software update for its Falcon Sensor product, which is designed to detect malicious threats at a computer system’s endpoints. The update resulted in the widespread crashing of computers using Microsoft Windows operating systems. Thus far, the update has only affected Microsoft users, and there has been no report of other operating systems being impacted. The system failure caused by the CrowdStrike update impacted a broad cross-section of industries, including airlines, banks, retailers, hospitality and more.
The event demonstrates a single point of failure for a complex, global information technology supply chain. Cyber insurers should use this event to evaluate policyholder supply chain dependencies, assess the potential for aggregation across commonly used technologies, and recalibrate risk tolerances accordingly.
Cyber Event Analysis: A Global Outage with Widespread Impact
Loss Components
Cyber insurance provides for broad coverage of business interruption resulting from network outage. The trigger for this coverage includes System Failure resulting from non-malicious acts, including human error. That coverage extends to Contingent Business Interruption (CBI) caused by an outage of a vendor on which an insured relies to operate its network.
Critical for evaluating network interruption claims will be the policy waiting period for which the network must be impaired before the policy responds. Typical cyber waiting periods vary depending on industry class and organizational size with 4–12 hours being most common.
CBI losses arising from a widely deployed technology present reinsurers with an acute risk for unexpected aggregation. Technologies with large market shares create potential single points of failure that can lead to systemic events yielding claims from a large number of insureds.
Modeling The Incident
While modeling scenarios do not account specifically for widespread outages due to software updates, there are sufficient analogous scenarios for estimating losses from the event, including business interruption and extra expense. These scenarios typically contemplate companies losing control over IT-related services, the impacts on customers and sales, and the potential for slow recovery.
While actual losses will vary from modeled instances based on the specific circumstances, such scenarios can establish a directional foothold for cedents to address systemic exposures. Guy Carpenter is currently engaged with the cyber catastrophe vendors for their analysis of this event and is conducting our own view to share with clients.
Impacts On Cyber Reinsurance
System failure losses will be in scope for traditional proportional and aggregate structures, which respond to all causes of loss. In recent renewal cycles, buying behavior selectively shifted toward targeted catastrophe covers, many of which respond to specifically defined catastrophic scenarios. Event-based products and the definitions behind them are unique to the cedent’s view of risk and how coverage was negotiated. Recoveries from event-based products will differ based on how each underlying wording differentiates coverage between malicious and non-malicious cyber incidents. As this incident progresses, Guy Carpenter will clarify its impacts on the assumptions around tail risk and the overall USD 15.5 billion global cyber industry moving forward.
Beyond Cyber Insurance
Given the magnitude and scope of this outage, we may see consequences that affect product lines beyond cyber risk, most prominently directors & officers (D&O) and property/casualty (P&C).
- D&O. We may see implications on the D&O towers for companies both involved in or impacted by today’s incident. In general, a 10% intraday stock drop for a publicly traded company may incentivize the plaintiffs’ bar to file a class action lawsuit. Subsequent share price moves and any ultimate recovery may also impact the likelihood of litigation. Historically, securities class actions arising from technology incidents have fared poorly. In addition to securities class actions, companies that are either involved in or impacted by the event may face increased exposure if they struggle to restore operations and may face shareholder derivative suits alleging the board’s breach of fiduciary duty.
- P&C. With the continued integration of information technology and operational technology, insures must also consider the physical consequences that may arise from technology failures. Potential exposure for P&C policies will depend on how insurers address cyber as a peril and whether the policy includes a “silent cyber” exclusion. Policies remaining silent on cyber risk may be exposed to ensuing bodily injury or property damage as a result of cyber-related system failure.
Guy Carpenter supports our clients through complex market developments. Our Cyber Center of Excellence analyzes reinsurance event language and stress tests its efficacy against potential cyber losses. The GC CyberExplorer® DataLake provides our clients with up-to-date intelligence for assessing the various dimensions of technology events, including software failure and network outages. Broad impact and large-scale events are part of developing a thriving insurance and reinsurance marketplace. Assessing events like today’s outage matures the view of catastrophe potential and advances structural considerations for protection.